Go beyond User Awareness Training with Comprehensive Human Risk Management
Calculate, reduce and monitor human cybersecurity risk with a suite of user-focussed cybersecurity tools. Ensure your business meets its cybersecurity insurance requirements.
Cybersecurity awareness training is broken,
Human Risk Management is the fix.
Turning your employees into cyber-savvy individuals who couldn't be tricked by even the smartest phishing email is a massive challenge. Most business only have the time or budget to run their cybersecurity awareness training a couple of times a year at best.
Unfortunately, this standardised model of teaching, quizzing and repeating, isn't regular enough. And it assumes equal knowledge across your end-users. They've all got their own strengths and weaknesses. So their cybersecurity training should be tailored to each individual.
Learning and evaluation should be regular to keep everyone on their toes. It should be low-cost, low-admin, and as automated as possible. And it should give you access to a suite of tools to understand and monitor human risk.
Traditional Awareness Training
-
Standardised - a one-size-fits-all approach to training that doesn't consider individual knowledge gaps
-
Irregular and time-consuming - running training sessions is time-consuming, so most businesses only conduct it a couple of times a year.
-
Disjointed - phishing simulations and policy adherence programs may be run sporadically, but often in different systems with limited reporting
-
Compliance Risk - many cybersecurity insurance policies require a high level of cybersecurity awareness and human risk management. Current methods may not meet the requirements.
Modern Human Risk Management
-
Tailored to each user - we start with a gap analysis to identify urgent risk areas, with training built for each individual that evolves as they learn
-
Comprehensive human risk solution - you'll have a single solution for:
- User-tailored training
- Risk reporting
- Simulated phishing
- Dark web monitoring and breach alerts
- Policy management
-
Automated - training, phishing simulation, monitoring and reporting are automated for less admin time spent on managing training
-
Demonstrate compliance - monitor risk over time, report on participation, and prove your compliance for cybersecurity insurance policies.
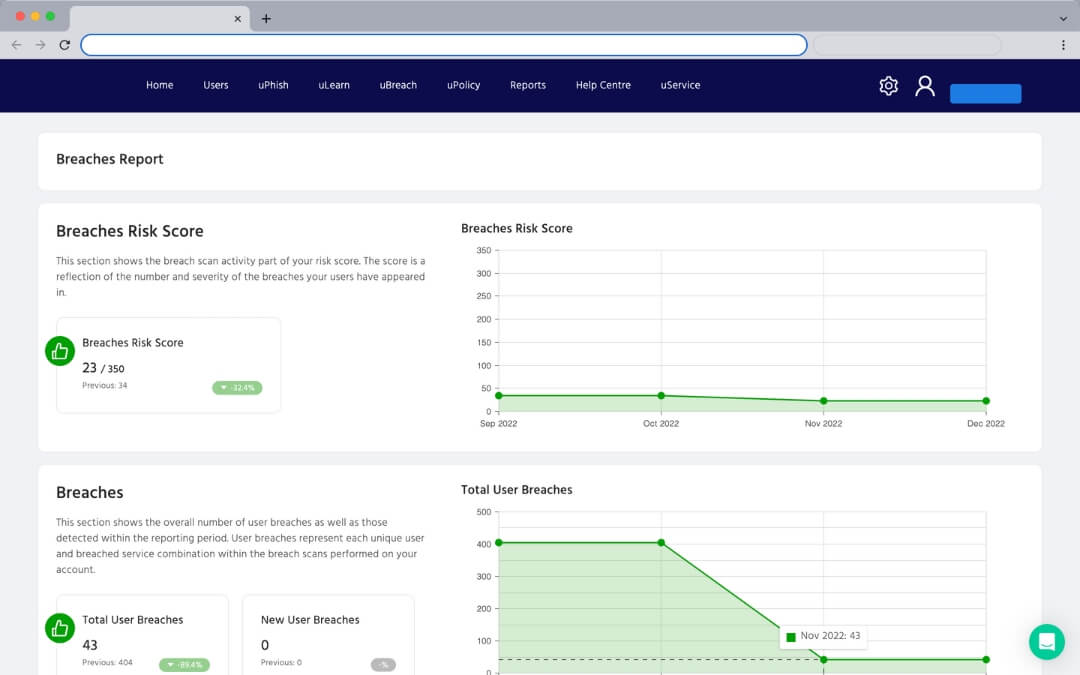
Human Risk Management
With every passing year, cybersecurity threats become worse and worse. Every month you see a new batch of phishing emails and another company that has become the victim of a massive data breach.
You can have the best Endpoint Detection and Response (EDR) solution, a fantastic firewall, and super secure servers, but these don't address the biggest risk of all... humans.
Humans are your biggest risk, but can become your strongest line of defence.
Human Risk Management (HRM) transforms outdated cybersecurity awareness training into a continuous learning and analysis program that helps you build a security-savvy workplace.
Our HRM helps you identify each employee's security knowledge gaps and tailors automated interactive training for each individual. You can monitor for data breaches and user data that has leaked to the dark web, run simulated phishing campaigns, and distribute policies to your employees with ease. All from an easy-to-use online portal.
Everything you need to manage human risk

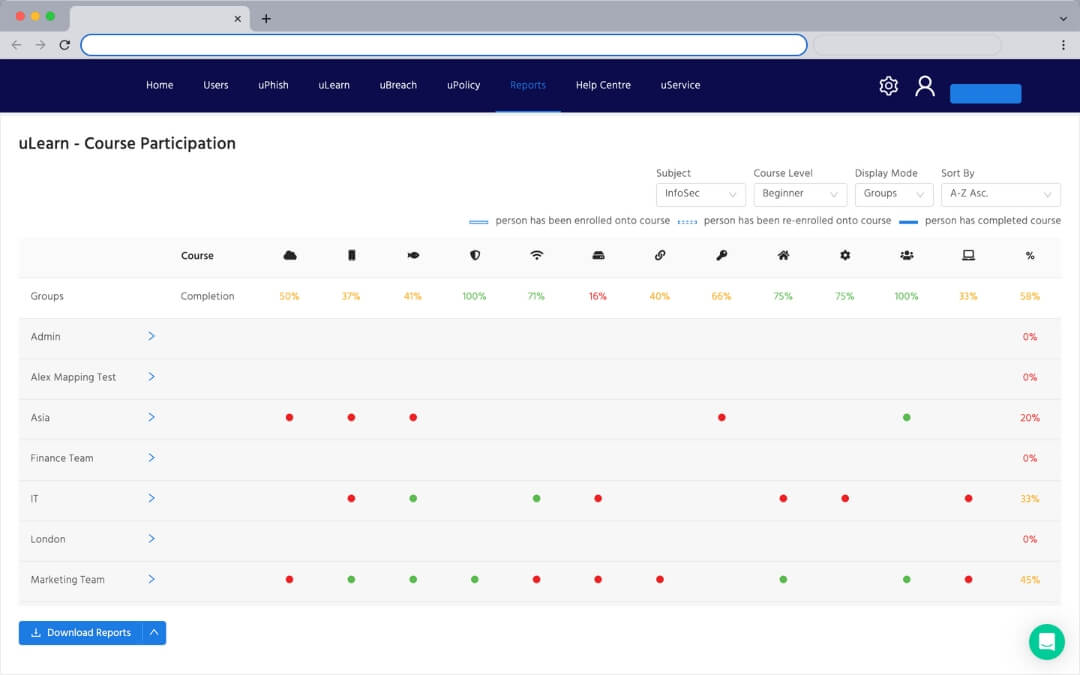
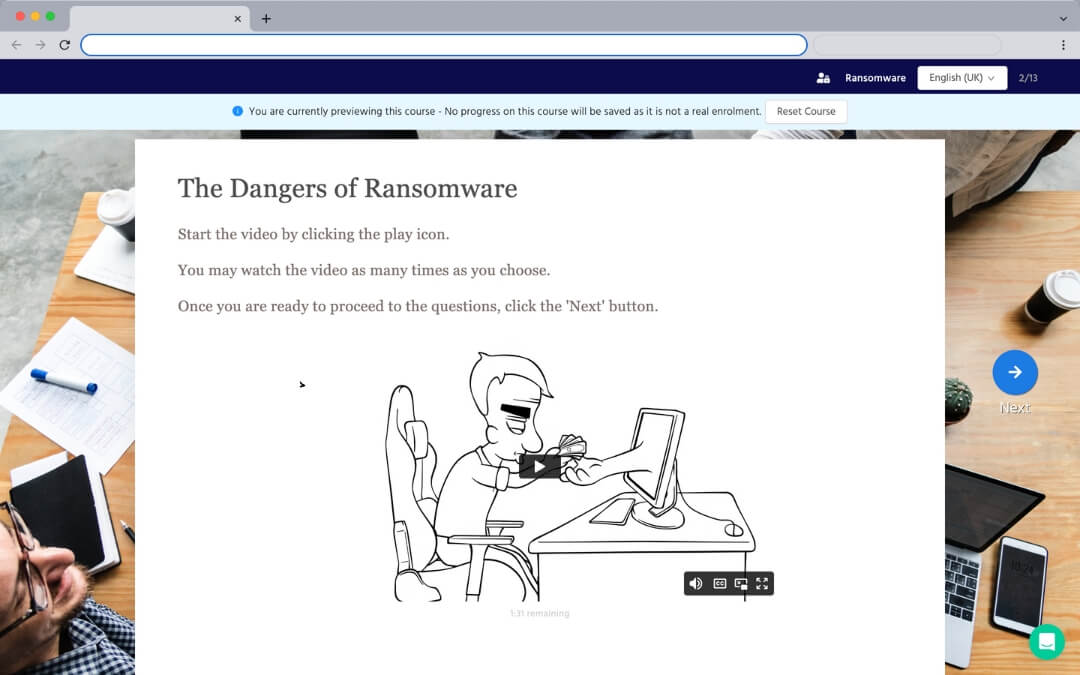
Security Awareness Training
Bite-sized video and interactive training focussed on infosec and compliance. Tailored to users.

Simulated Phishing
Trackable simulated phishing campaigns with ready-made and custom templates.

Dark Web Monitoring
Dark web scanning that detects exposed user data that could be leveraged in a cyber attack.

Policy Management
Centralised library of customisable policy templates that simplifies and tracks employee policy acceptance.

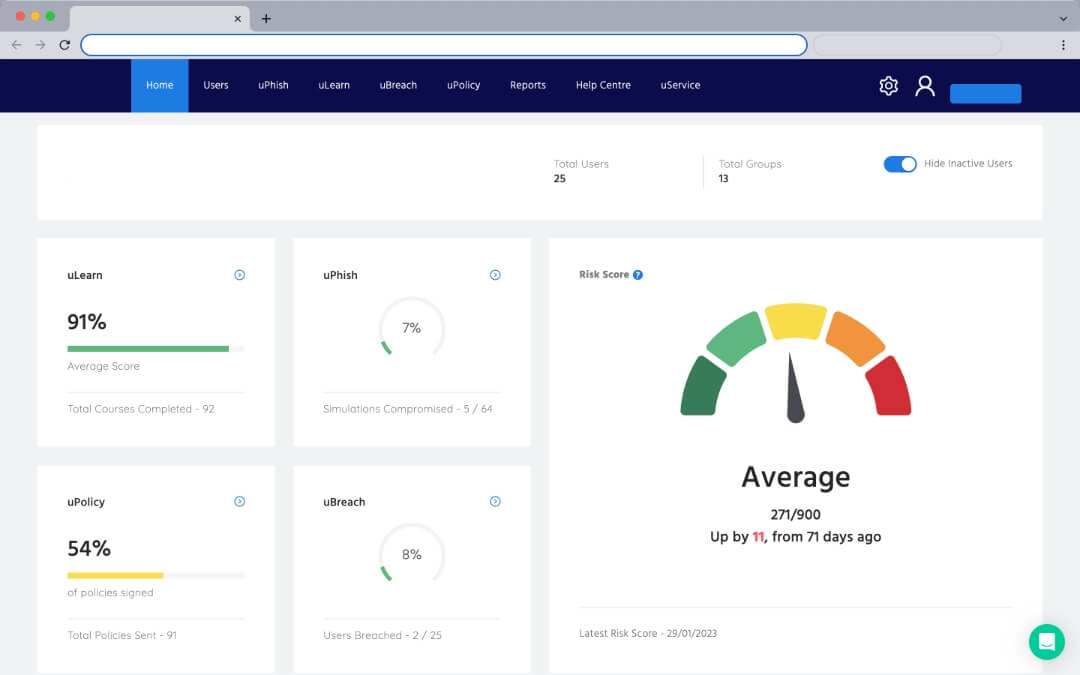
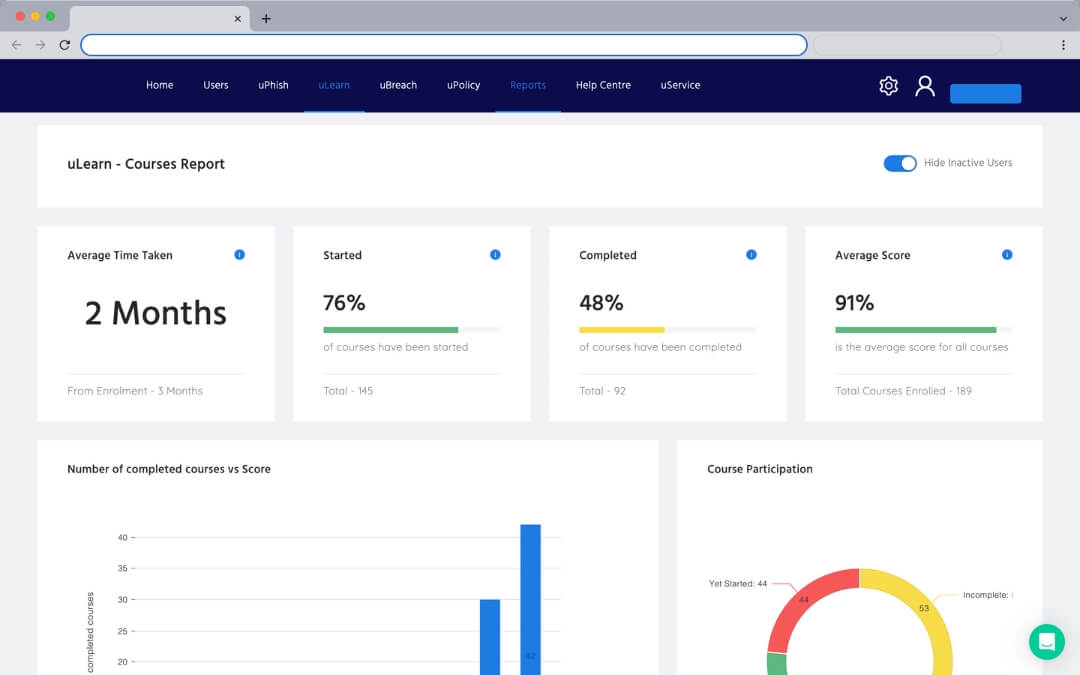
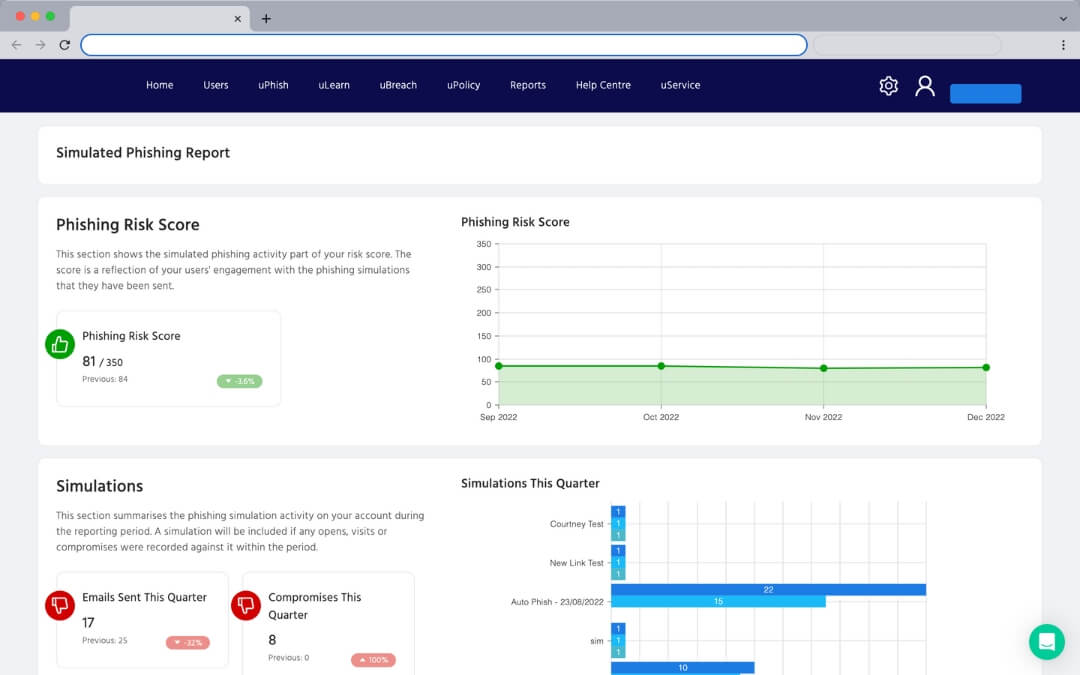
Human Risk Scoring
Company-wide human risk scoring that gives a high-level snapshot of current risk.

In-Depth Risk Analysis
Dive into human cyber risk at the individual level, perform gap analysis, view user performance and trends.
The challenge of human risk management
%
Of businesses saw reduced susceptibility to phishing after cybersecurity training
(Source: uSecure)How at risk are you, right now?
How many of your users would plug in a random USB that they found in your lobby? Have any of your employees' usernames or passwords been caught up in a data breach? Do you have regular cybersecurity training set up that addresses your employees' weak areas?
Work with us to determine your current level of risk, and create an ongoing automated Human Risk Management program.
1. Human Risk Report
To assess your current level of risk, we'll perform a FREE Human Risk Report that includes a dark web scan, phishing simulation and domain analysis.
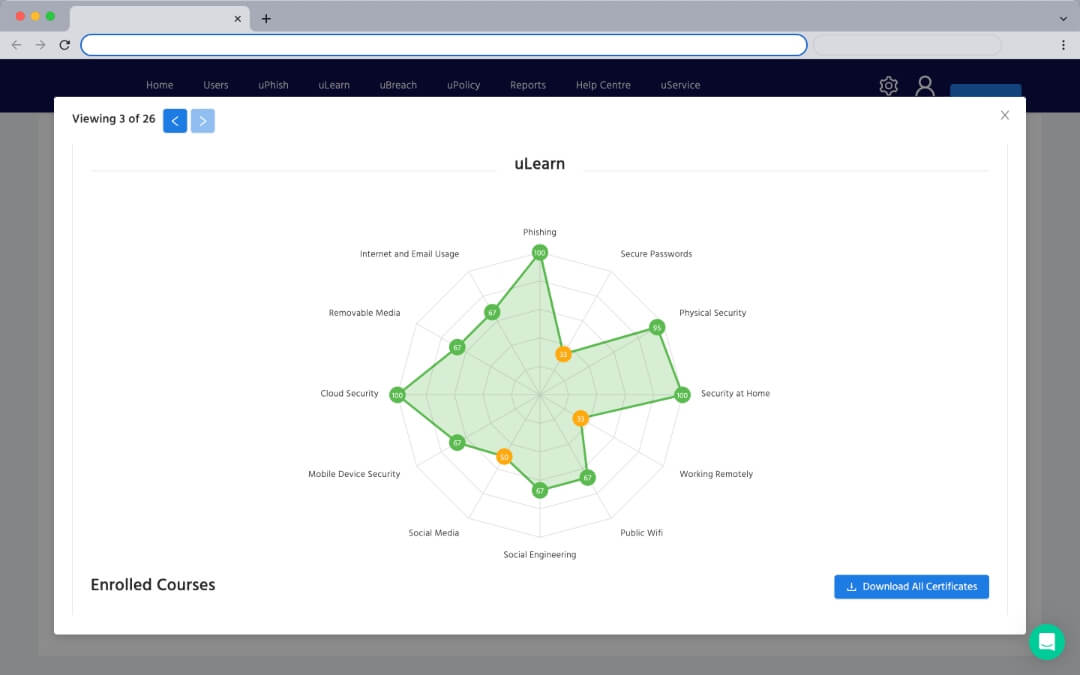
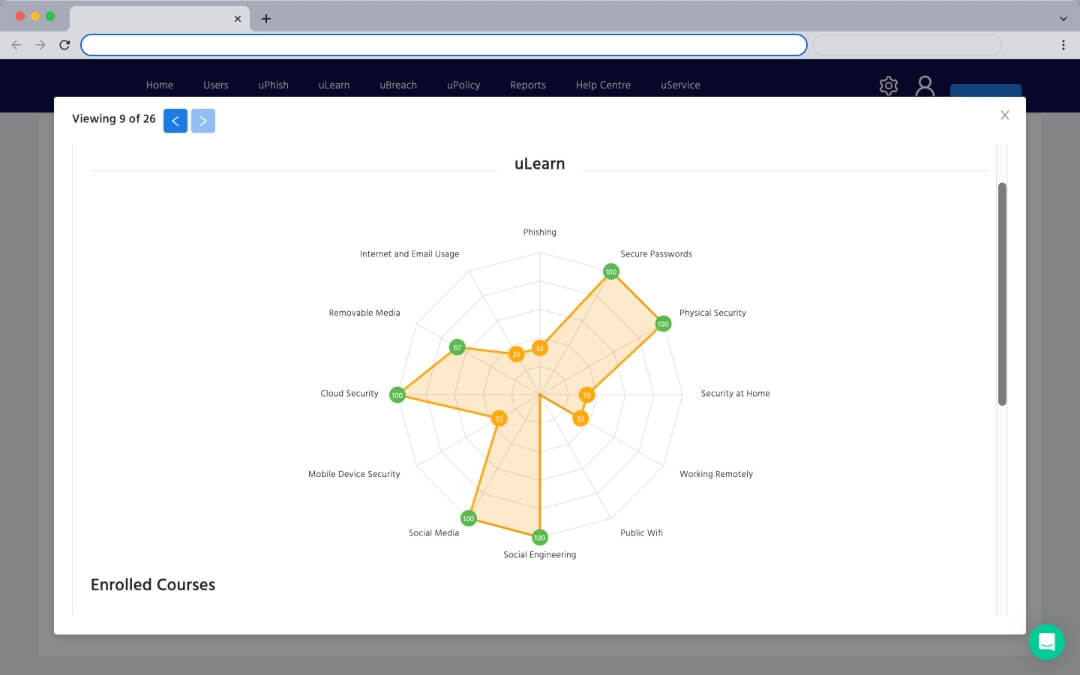
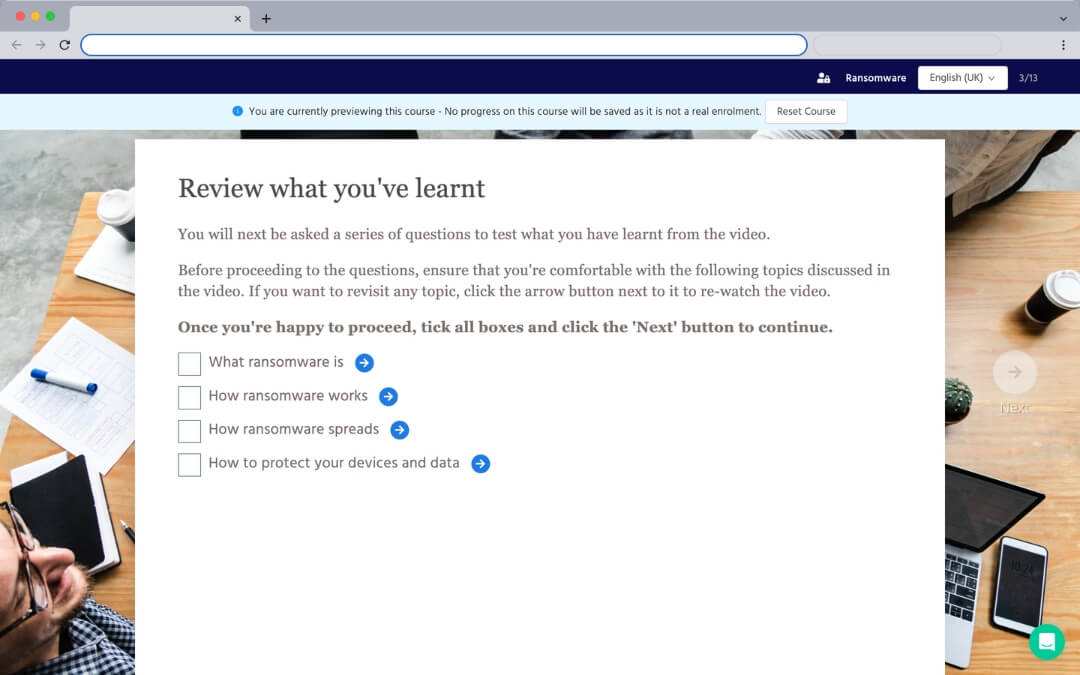
2. User Gap Analysis
A sample group of end-users complete a 15-minute questionnaire that scores them on their overall cybersecurity knowledge and identifies any risk areas.
3. Start Reducing Risk
Your staff will be enrolled in their personalised HRM training plan. Bite-sized training and phishing simulations are automatically scheduled.
4. Monitor and Improve
Understand the impact of your HRM and your ongoing risk with regular summary reports outlining training performance, phishing results and policy compliance.
Understand your human risk
Do you know how easy it is to create a lookalike domain to trick your staff? When was the last time one of your end-users clicked on a phishing email? How many data breaches have your end-users been caught up in?
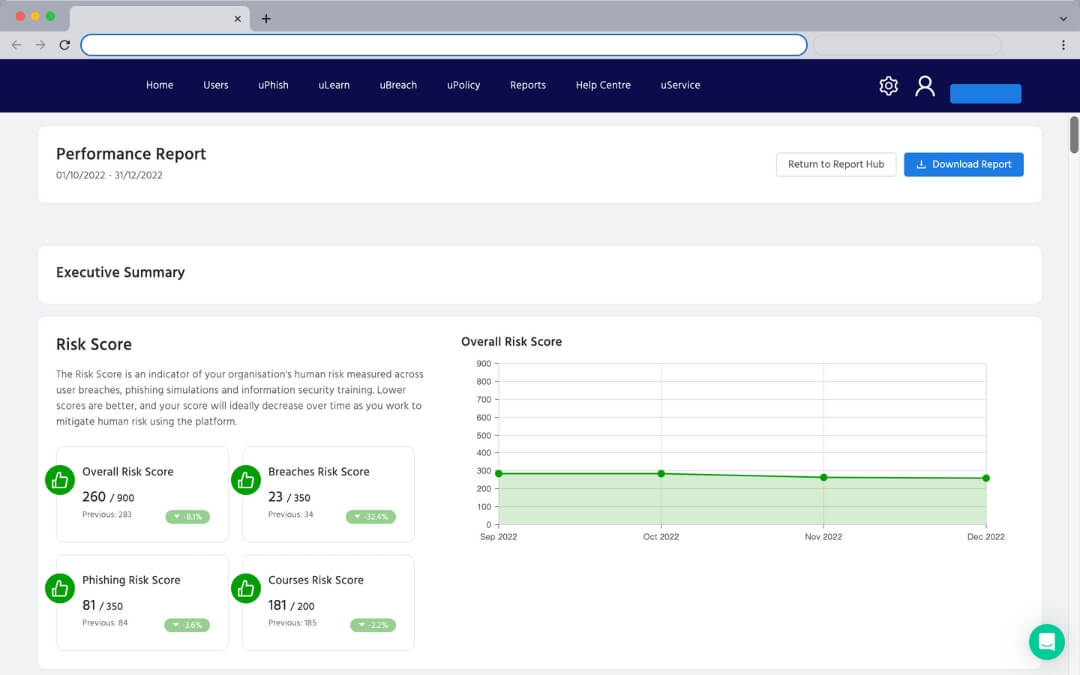
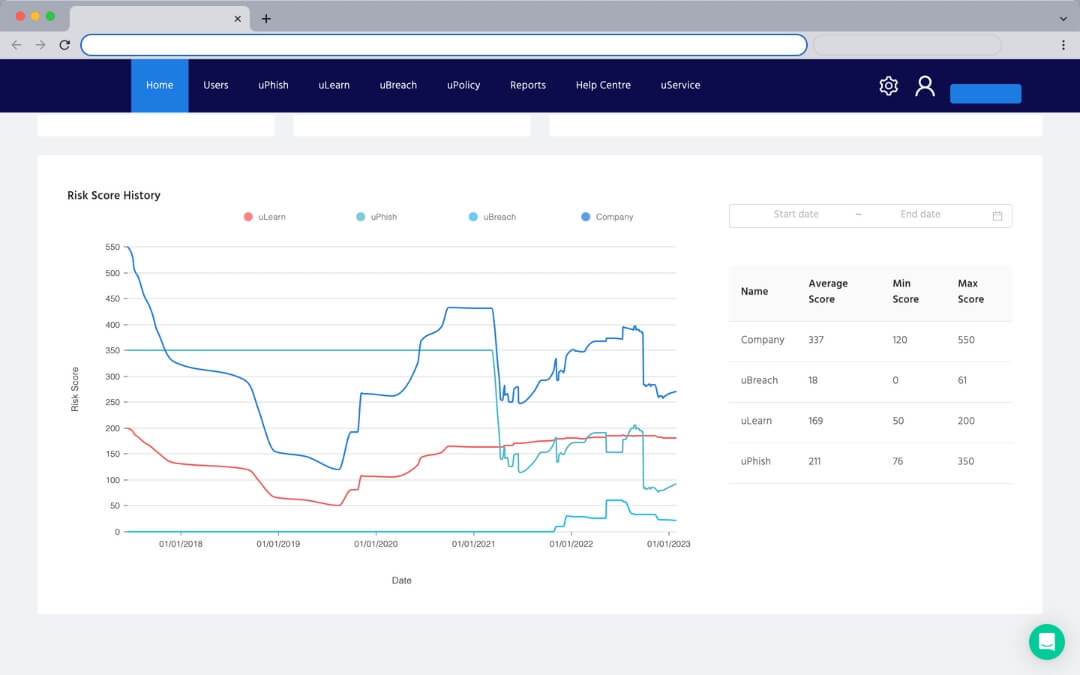
To understand your human risk, an initial Human Risk Report will identify your current risk score and highlight any key issues. But one-and-done isn't enough. Enabl's HRM platform provides ongoing human risk metrics and progress reports that enable you to take action.
Detect high-risk areas
Identify compromised user data, find out who will fall for a phishing scam, and average cybersecurity awareness scores across your business. Take action to strengthen your first line of defence.
Measure training impact
Track the progress of your cybersecurity awareness levels month-by-month and continue to focus on weak areas that need improvement.
Meet your compliance needs
Automate tailor-made cybersecurity training
Running cybersecurity awareness training isn't easy. It can be time-consuming, employees can be disengaged, and C-level stakeholders may not want to set aside the time or budget for regular training. It's time to get rid of the standardised one-and-done model.
Enabl's HRM solution gives you the tools you need to create a robust and regular training program. Tailored to individuals, automated and easy-to-use, reports for tracking progress and compliance.
Identify risk areas to focus on
Everyone has different strengths and weaknesses, so training should never be generic. A quick gap analysis questionnaire identifies each user's weakest areas of security, building unique risk profiles for all your staff.
Tackle risk on an individual level
Once you know your employees' weak areas, the HRM platform automatically enrols users into personalised training plans that match their risk profiles and focus on high-risk areas.
Automatically deploy customised training
Take back your time for other tasks. Set up a training schedule that works for your team and automatically schedule training, follow-up emails and reporting.
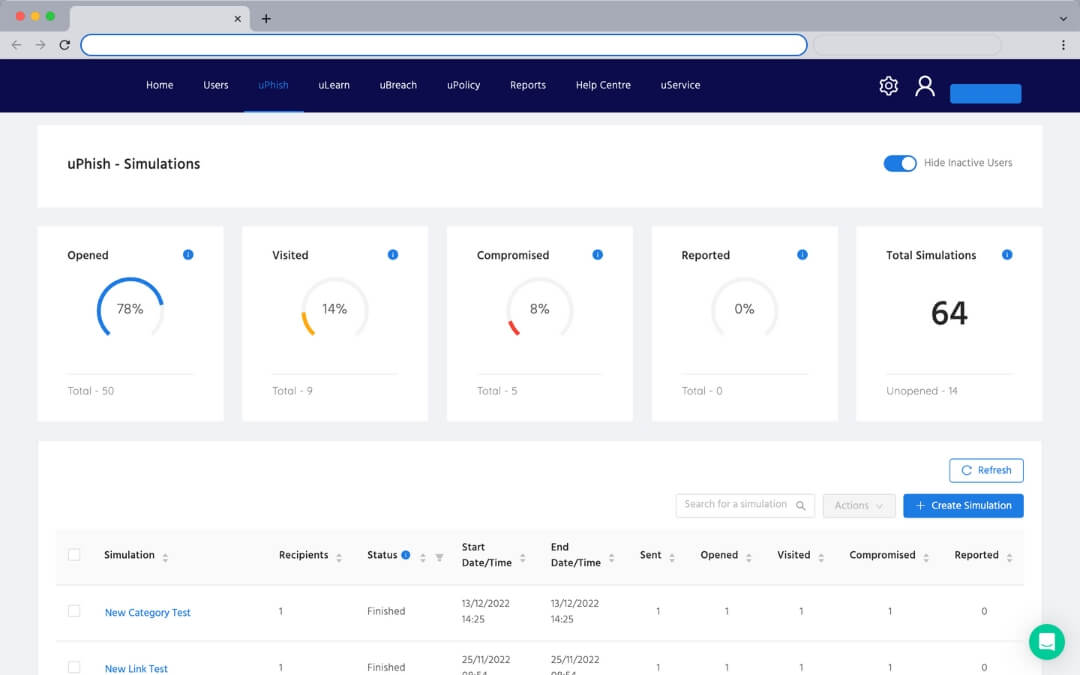
Keep your team on their toes with simulated phishing
With 36% of data breaches involving phishing, your team need to be prepared. Create and run phishing simulations to identify staff who need additional training and ensure they're ready for real attacks.
Automatically schedule phishing simulations
Get phishing in minutes with simple configuration. Turn on automated phishing to create a schedule of ongoing simulations to measure resilience over time.
In-depth reporting
Marketing thinks they've got the best email reporting. Give them a run for their money with in-depth analysis of campaigns. Identify team and individual risk and focus your training plan.
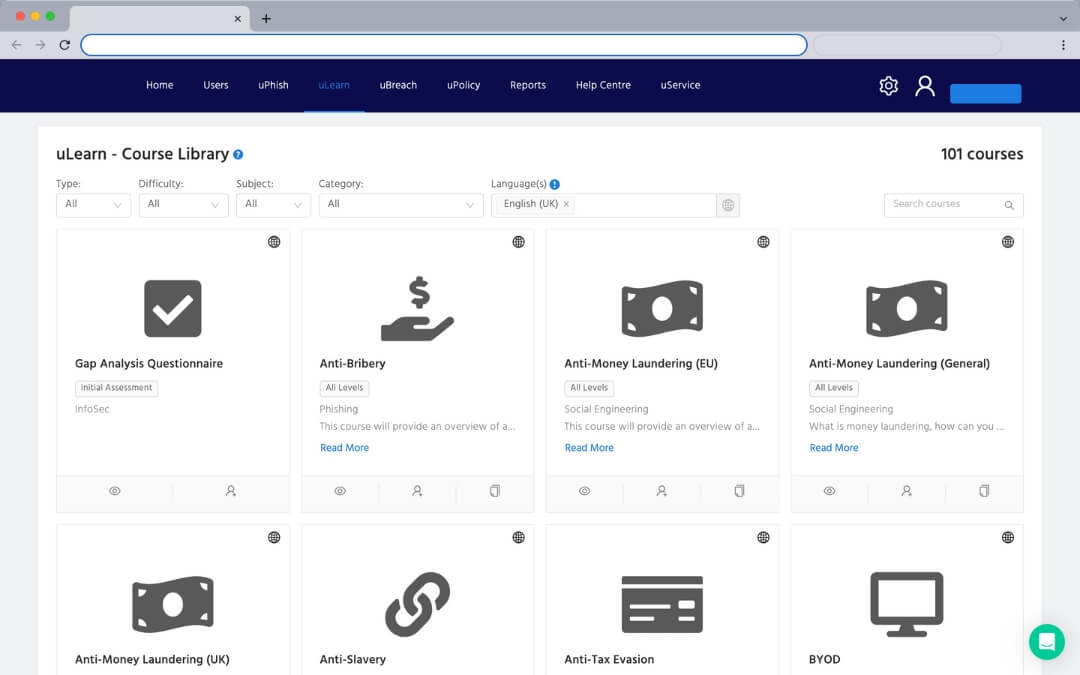
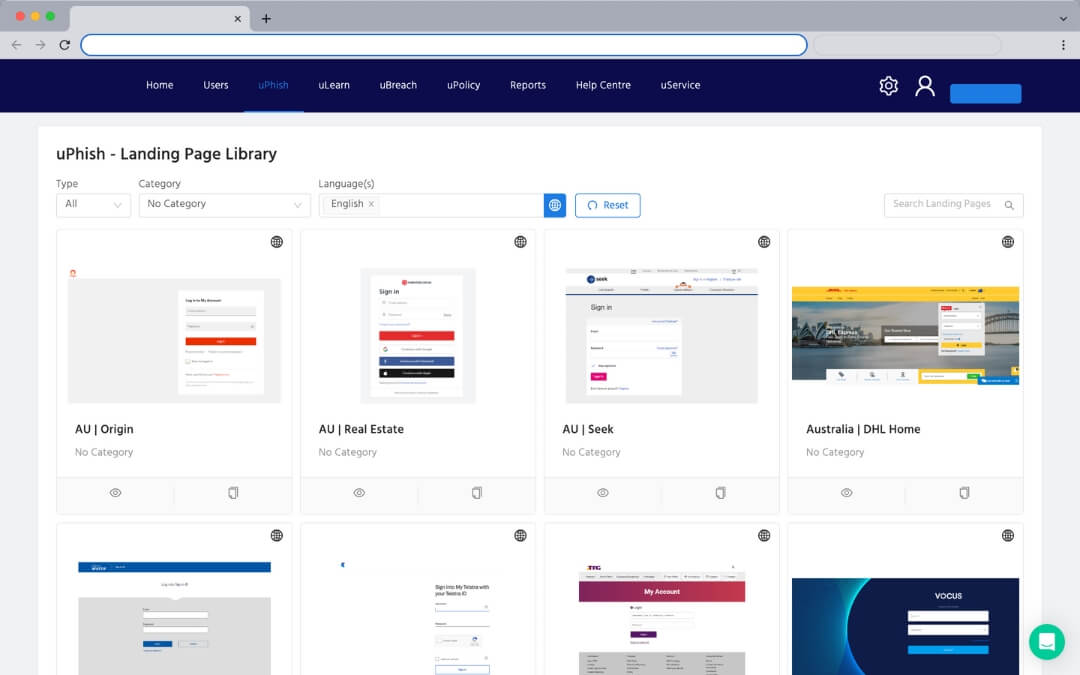
Comprehensive template library
Utilise a range of realistic ready-made templates from trusted brands. Some of these include:
- Banking - ANZ, Commbank, NAB
- Online shopping and deliveries - Coles, JB Hi-Fi, AusPost
- SaaS and Software - Microsoft, HubSpot, Xero
- Government - MyGov, Transport Department
- Or build your own templates from scratch
Challenge staff with spear phishing
Ensure your staff are prepared to spot the little details. Run targeted spear phishing simulations impersonating internal staff.
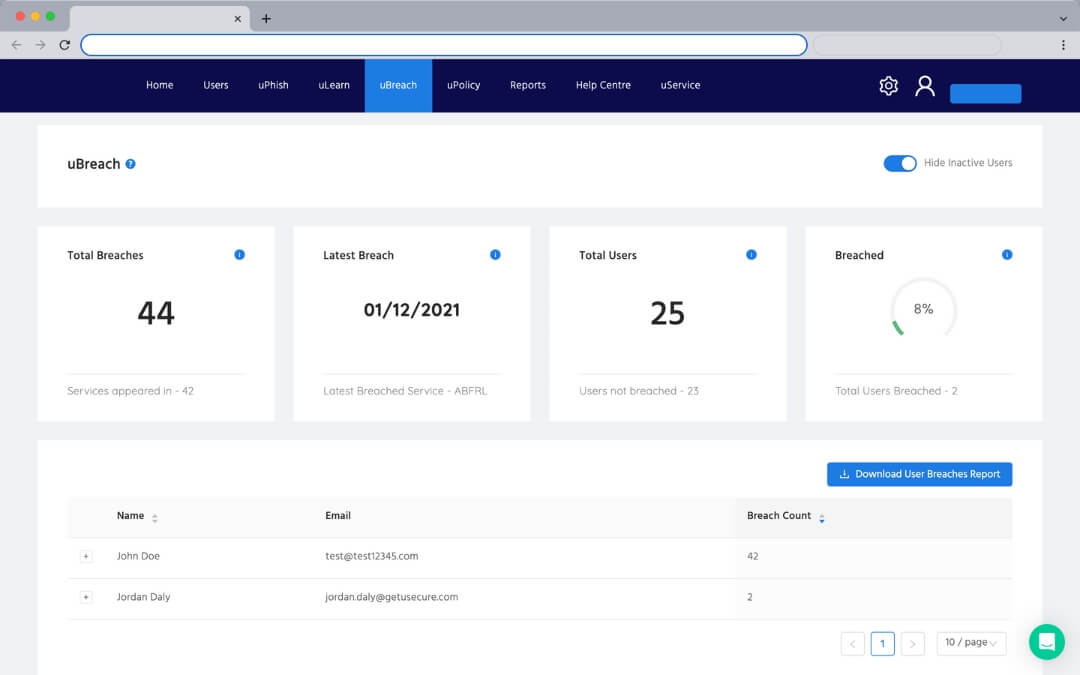
Watch for data breaches with dark web monitoring
Data breaches are on the rise every year. Recently, we've seen high-profile data breaches at Canva, Optus, Mediabank and Service NSW. With 64% of people reusing passwords across multiple accounts, each data breach could leave you vulnerable.
Using our Dark Web Monitoring, you can rapidly identify users caught up in data breaches, and take action to mitigate any risk.
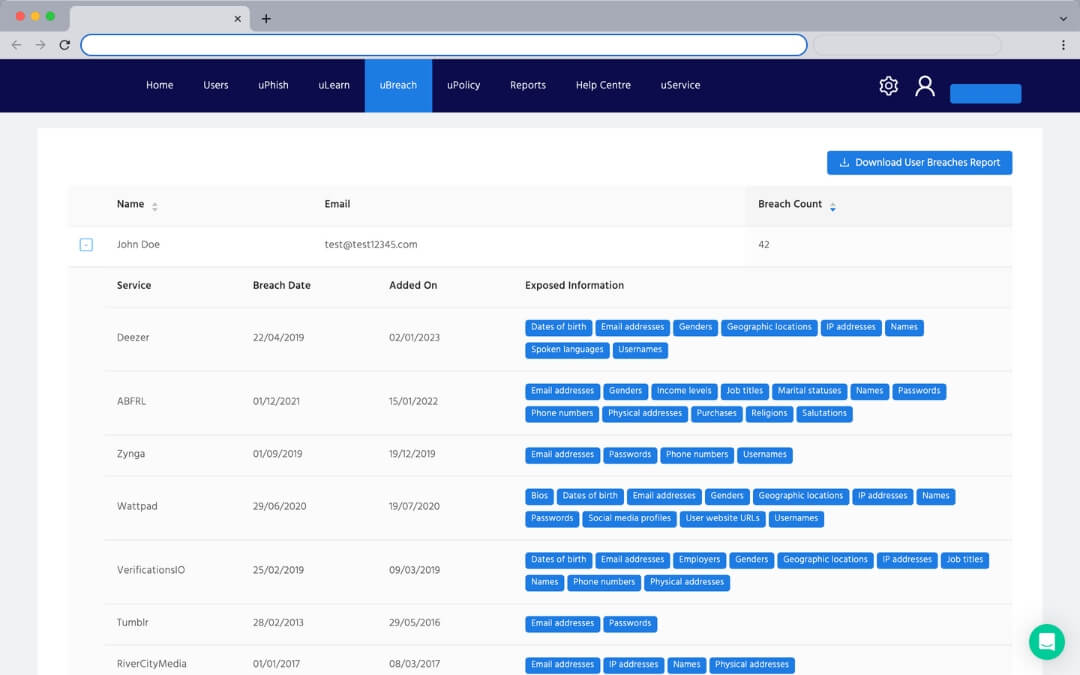
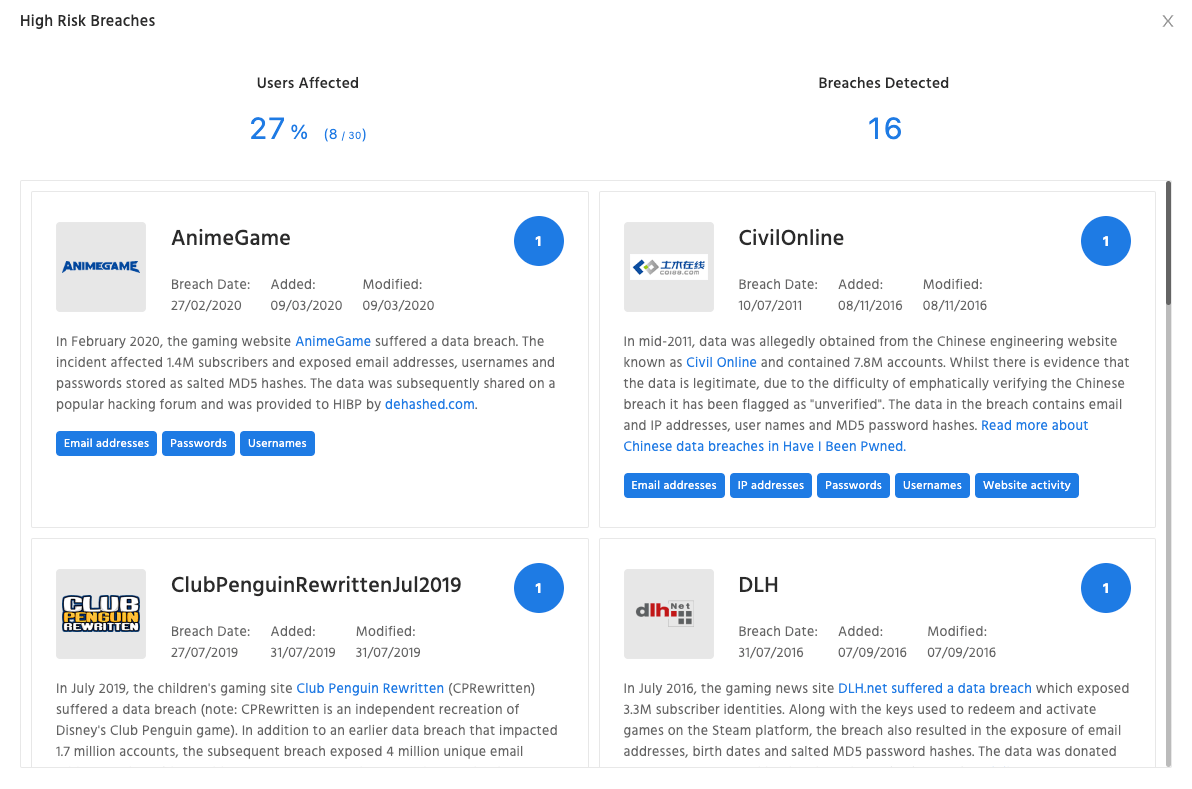
Identify your breached data
Our HRM conducts a search through data dumps, paste sites and breached data forums to report back on which email accounts have been compromised, what data may be exposed, and what breaches led to the exposure.
Monitor for new exposures
Data breaches are continuously monitored with real-time alerts notifying you of any new data breaches.
Drive secure behaviour
By identifying employees caught up in data breaches, you can enrol these at-risk users on password and web safety training.
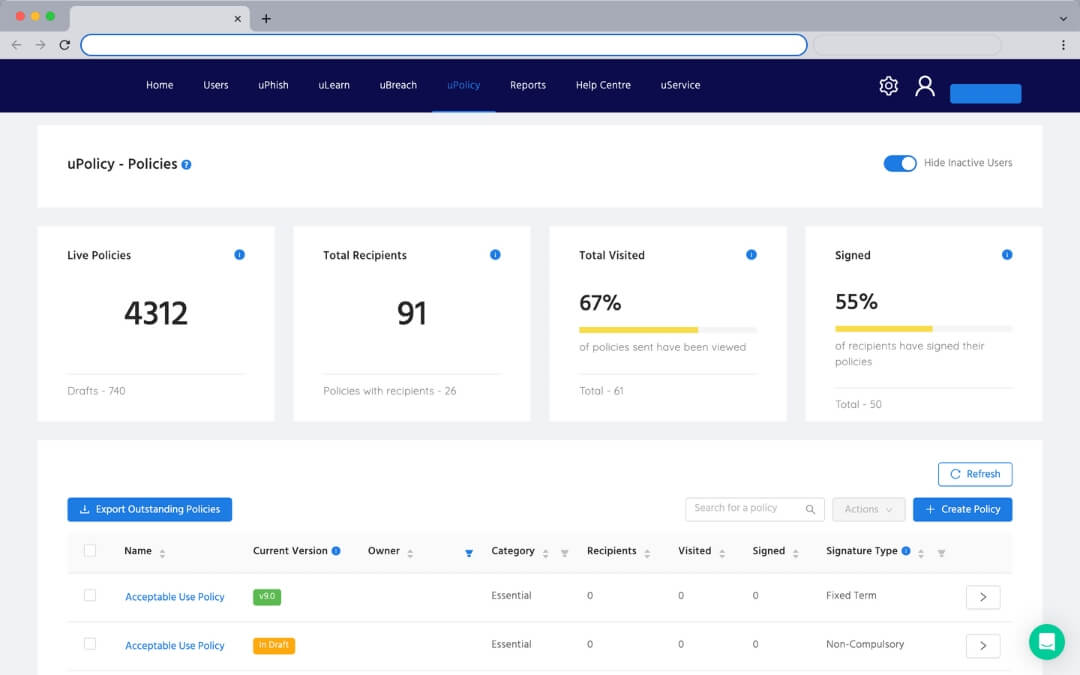
Easy, automated policy management
Traditional policy management is a pain. Manually creating Word Docs. Managing different versions. Sending out updates to be accepted by staff. Not knowing the approval status of policies across the business.
It's time for an easier way to managed your policies and ensure your people are complying with them.
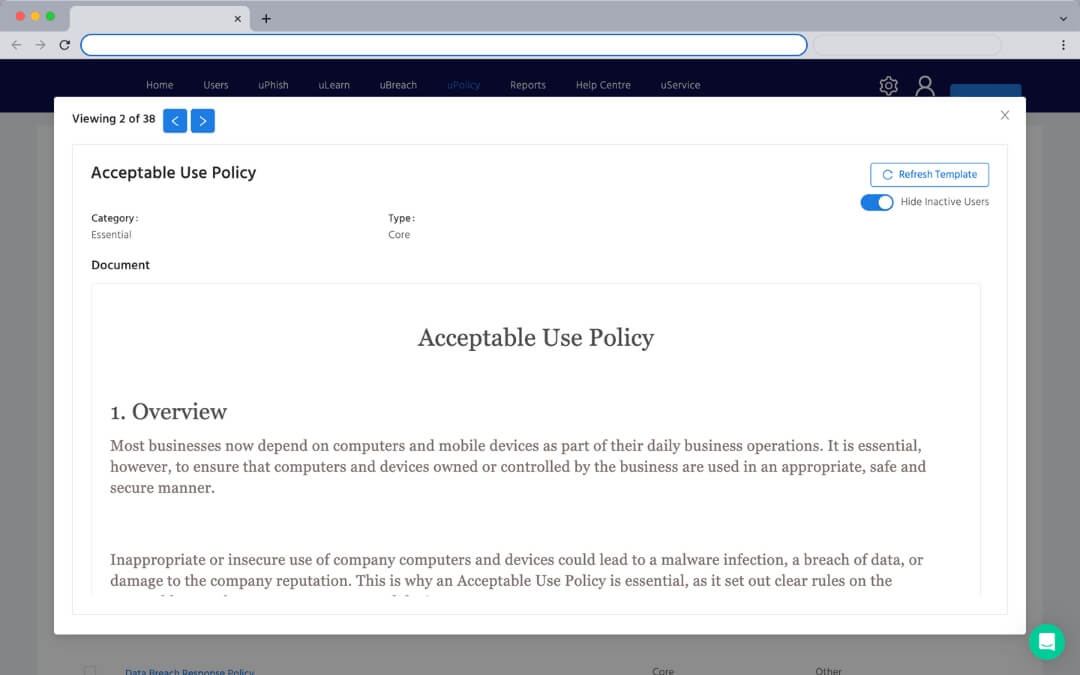
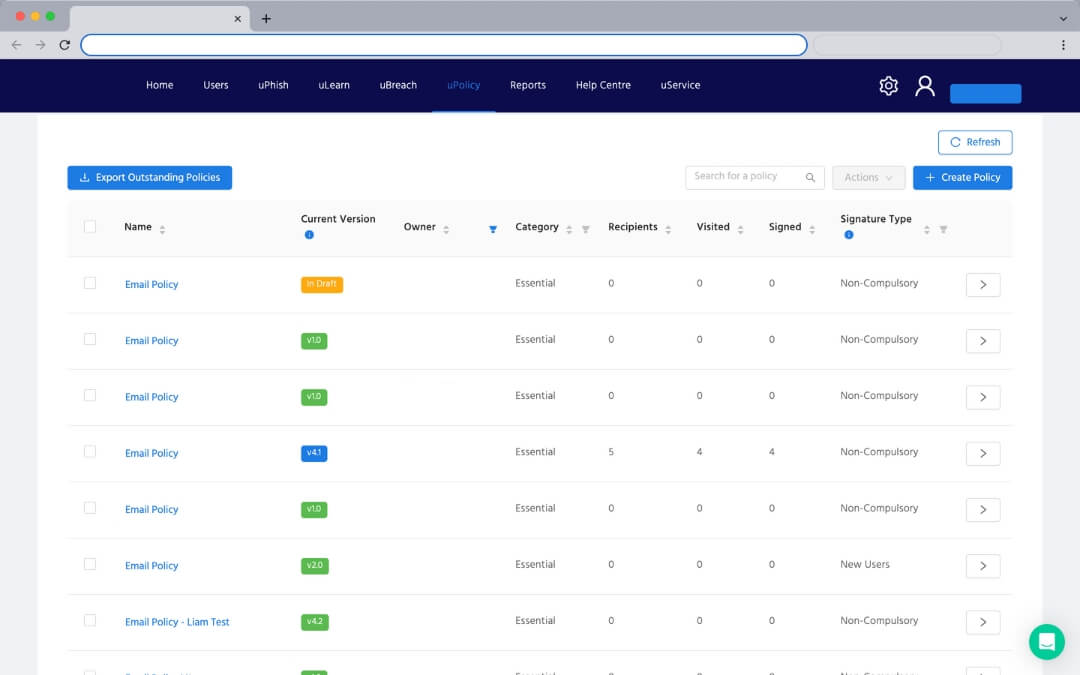
Centralise policy creation
Move all your policies into a single web portal. Access a library of customisable policy templates or create your own from scratch.
Update and communicate changes
Amend policies, track version history and automate policy change announcements via email. Employees can access and approve policies in minutes with built-in eSignature approvals.
Monitor policy compliance
Track which users have viewed and approved policies. Enable email reminders to outstanding employees. Provide external access to auditors or download policy reports.
Transform your cybersecurity training
Interested in taking your cybersecurity training to the next level? Get in touch for your free Human Risk Report.